|
|
|
|
 Far Far |
 WinNavigator WinNavigator |
 Frigate Frigate |
 Norton
Commander Norton
Commander |
 WinNC WinNC |
 Dos
Navigator Dos
Navigator |
 Servant
Salamander Servant
Salamander |
 Turbo
Browser Turbo
Browser |
|
|
 Winamp,
Skins, Plugins Winamp,
Skins, Plugins |
 Необходимые
Утилиты Необходимые
Утилиты |
 Текстовые
редакторы Текстовые
редакторы |
 Юмор Юмор |
|
|
|
File managers and best utilites |
Best VPN for Tor: How to Use Tor and VPN. Vpn tor браузер
Vpn tor browser Free Download for Windows
3 The Tor Project, Inc. 24 Freeware
Tor Browser Bundle is a set of tools that lets you access Tor network.
26 b.VPN Service 1,177 Shareware
Redirects your Internet traffic through various virtual private networks.
227 S.A.D. 48,314 Shareware
Surf anonymously and access restricted/blocked websites.
53 KeepSolid Inc. 6,470 Shareware
Surf the Web anonymously to protect your data and your privacy.
8 PopNet Media LLC. 165 Shareware
Surf anonymously, prevent hackers from acquiring your IP address.
12 Overplay 879 Freeware
OverPlay VPN, change your IP address to one in another country.
14 Avira Operations GmbH & Co. KG 24,064 Freeware
Make your internet connection secure, private, untraceable and unlock websites.
1 Globus Partners Ltd. Shareware
HOW OUR VPN, VPN+TOR, CLOUD VPN SERVICE COMPARES.
Lars Werner 4 Freeware
Adito sofware is an open-source, browser-based SSL VPN solution.
2 ADTelly 12 Freeware
ADTelly Browser will allow you to seamlessly connect between our UK and US VPN.
AnexGATE Demo
Is a form of VPN that can be used with a standard Web browser.
12 Globus Partners Ltd. 378 Freeware
Globus VPN Browser allows you to access to any restricted website.
1 GOM 92 Freeware
Browser extension that lets you to access blocked sites using the Gom VPN.
1 Webzilla Apps Inc. 25 Freeware
A free web browser with a built-in VPN service to protect your identity.
softwaretopic.informer.com
How to Use Tor and VPN
A VPN, or Virtual Private Network, is used to encrypt data and anonymize its users. Consumer VPNs are used for all kinds of purposes: bypassing censorship, watching another country’s Netflix and ensuring that neither their ISP nor anyone else can snoop into what they’re doing online.
VPNs work through a variety of VPN protocols. VPN protocols determine how a VPN routes and manages the data going through it. You’ll enjoy different speeds and different levels of security depending on what VPN protocol and VPN provider you happen to be using. While some focus on speed over security (or vice versa), it’s generally a good idea to find one that can do both well.
In this article, we’re going to discuss the best VPNs to use with Tor. We’re also going to introduce you to how Tor and VPNs can be utilized together to safeguard your privacy without too much compromise on performance.
What is the Best VPN for Tor?
- Subscribe to one of the VPNs in this guide.
We highly recommend ExpressVPN (save 49% here), but you’ll also find two more world-class VPN services that will work great.
- Download and install the VPN’s client software.
- Connect to a VPN server of choice.
- Now you can enjoy unrestricted access to any websites.
Understanding Protocols: OpenVPN and L2TP/IPSec
The most widely used VPN protocols are OpenVPN and L2TP (with IPSec encryption).
OpenVPN is a VPN protocol that’s commonly seen implemented with third-party applications. The “open” in its name stems from the fact that it’s open source, which means that anyone can edit and improve its source code. Due to robust developer support, OpenVPN boasts some of the best security out there, and thus far has not been broken. It focuses on security, but does so without an excessive compromise on speed.
L2TP is another VPN protocol, but requires IPSec to be implemented alongside it. This is because L2TP is technically just a tunneling protocol, while IPSec is an encryption protocol; the two combined make one of the most popular VPN protocols out there. There are no known vulnerabilities, as L2TP is heavily focused on security. Like OpenVPN, its speed isn’t bad either (depending on the day, it might even be a little faster).
What is Tor?
Tor is not only an incredibly interesting piece of software, it also has an incredibly interesting history. Despite its modern day association with cyber criminals, its underlying technology (known as “onion routing”) was developed by US Naval Researchers and DARPA.
Onion routing is known as such because it relays messages through a node network of proxy servers, each of which adds a new layer of encryption to any data passed through it. Each encapsulated message can be peeled away in the application layer of a protocol stack, much like peeling off the layers of an onion. In theory, the end result of transmission via Tor is that a message should be nigh untraceable to its originating IP address. While Tor itself isn’t vulnerable, the opposite ends of the relays (the original user and the exit node) can still be compromised.

The media has portrayed Tor users as criminals or creeps, but in reality the utility of internet anonymity attracts people from all walks of life. In reality, there is a rather large number of legitimate usages for Tor including whistleblowing, anonymous communication, journalism, and much more. Ultimately Tor is only a tool, and how it is used depends entirely on the person who is using it.
The idea of being compromised on Tor remains a scary one, however. Even if you aren’t a shady type, there are a large number of less scrupulous Tor users out there, and they may not be friendly. If they learn your personal information, it could have some truly scary consequences. In general, as long as you practice good browsing and don’t give any personal information out on Tor, you’ll be safe. The chance of actually getting nailed on the Tor network by normal means is infinitely small, and isn’t worth the worry for most users.
Why use Tor along with a VPN?
Let’s say you’re not most users, though. Say you’re a whistleblower, like Edward Snowden, or you’re doing something of similar weight that absolutely must not be detected by anyone. Whether you fit that description or you just want to be careful for the sake of being careful, using a VPN with Tor may just be the answer that you’re looking for.
How can I use Tor with a VPN?
In this section, we’ll cover two distinct methods for the utilization of VPNs alongside Tor. There are benefits to both solutions.
Method 1: VPN-to-Tor
The first method of using Tor with a VPN is to route your VPN traffic into the Tor network. Since your VPN will hide your traffic from your ISP, using Tor within it will effectively hide that you’re using Tor at all, which is useful if people are actively searching for evidence of Tor usage/connections, or your ISP restricts usage of Tor altogether.
Fortunately, the execution of this method is pretty simple. All you need to do is enable your VPN, verify that it’s working properly, and open your Tor browser of choice (whether that’s the official Tor Browser or Whonix, a popular alternative).
Method 2: Tor-to-VPN
This second method effectively prevents any possible interception of your Tor traffic, but won’t hide your Tor traffic from your ISP like the first method does. If you want to ensure that it’s impossible for anyone on the Tor network to track your data back to you, this is the method to go with (though it is much more difficult to set up).
This method requires either a dedicated PORTAL router or Whonix. We recommend Whonix for convenience’s sake if you don’t already own a PORTAL router. Using Whonix will require that you have VirtualBox as well, since Whonix is technically its own OS. Here’s a tutorial on that.
Once you’re in your Whonix workstation or you’re connected to your PORTAL router, sign into your VPN network. Congratulations: your Tor traffic is now completely secure against all eyes but your own!
Recommended VPNs
Now, we’re going to recommend our top VPNs for use with Tor. Keep reading to learn more about each of these solutions and which might be right for you.
1. ExpressVPN

ExpressVPN is one of the most popular VPNs on the market. This is because of its sheer level of performance, which means it’s one of, if not the fastest VPN service out there. In addition to speed, ExpressVPN also offers VPN split tunneling, which will allow you to route only certain applications (say, Tor) through your VPN while using your normal connection for other stuff (gaming, for instance).
ExpressVPN is also one of the options on this list that offers a .onion site and Bitcoin payments. Along with their privacy-sensitive logging policy, these features give you the ability to create a completely anonymous account on ExpressVPN’s network that can’t be traced back to you. In fact, they don’t even want to track back to you!
While ExpressVPN does technically have logging, this logging is extremely basic: only the dates when you connect and the amount of data that is used within that date. This is also matched alongside your account information, but not your IP address. And even if it were, you using Tor to access your VPN would negate that as well.
In addition to great performance and the convenient split-tunneling feature, ExpressVPN supports Netflix spoofing. If you want to use your VPN to access other country’s Netflix as well, feel free, just be sure not do the Netflix viewing through Tor, as it’ll be quite slow and Netflix might actually detect your Tor usage.
Honestly, ExpressVPN has very few downsides to speak of. Besides its price, which is higher than any other VPN on this list and higher than most offerings you might see, ExpressVPN really doesn’t have any outstanding flaws. It’s just an incredibly solid VPN offering.
For that reason, it’s our top recommendation.
Try ExpressVPN absolutely RISK FREE with a 30-day money-back guarantee–no questions asked!
2. IPVanish
A passing glance will tell you that IPVanish has a no-frills VPN solution designed for one thing and one thing only: giving you private traffic.
While the lack of extra features may be a downside to some, that shouldn’t matter much to you. You probably don’t need a VPN to use Netflix if accessing Tor and the Dark Web is your main concern, and IPVanish isn’t really geared toward anything else. Instead of bothering with all that, it focuses on pure performance reliability, and is easily one of the most reliable solutions on the market.
AddictiveTips readers get a special a 60% discount on the yearly plan for a low monthly payment of just $4.87 per month!
This is ideal, since any weak link in your connection could expose you. With IPVanish in play and its automated DNS leak protection, you should be completely safe. Additionally, IPVanish claims that they don’t keep logs at all, which makes it ideal from a privacy standpoint.
In fact, if you want to go all the way, you can sign up for IPVanish from within Tor, use an anonymous email address and pay with Bitcoin. Done that way, your IPVanish traffic will never be able to be traced to you, even if they are logging it, because they’ll have no idea who you are.
If you’re not completely happy using IPVanish, get your money back with a 7-day satisfaction guarantee!
3. NordVPN
Get a 72% discount when you sign up for NordVPN’s 2-year subscription special at just $3.29 per month!
Because NordVPN is based outside of the US, it is legally able to maintain a firm no-log policy. This means its users don’t get saddled with the liability created by mandatory logging laws.
While some logging may be tolerable in a VPN context (the most basic kind), no logging is still better than some logging. NordVPN is another great option for this usage scenario based on that alone.
In addition to a no-log policy, NordVPN supports Double VPN. Double VPN routes your VPN traffic through two VPN servers instead of just one of them, like most VPNs. When implemented in tandem with Tor, your data becomes virtually impossible to track, since its origin is buried under so many layers of abstraction and encryption.
However, using Double VPN comes with a performance penalty. Considering Tor’s already low speeds, that may end up being a problem if you’re short on time and need your Tor browsing to be as fast as possible.
Additionally, NordVPN may occasionally have trouble on its initial connection. While this can usually be fixed by simply trying again, this can be quite annoying to deal with in the long run, especially if the implementation of Tor makes it a recurring issue.
Finally, Nord offers Netflix spoofing. If, for some reason, you want to enjoy Netflix from another country while also browsing Tor, NordVPN makes that possible. NordVPN also has the most compatible platforms out of all the entries on this list.
It’s a worthy option, but whether or not it’s the best one is up to you.
NordVPN prioritizes customer satisfaction, and offers a 30-day money-back guarantee!
Conclusion
With all features considered, we recommend ExpressVPN for most Tor users. If you’re leery about its basic logging, however, you can always elect NordVPN or IPVanish.
IPVanish and NordVPN is the more interesting grudge match. IPVanish is more reliable than NordVPN, and cheaper at that. However, NordVPN is much more feature rich and supports more platforms (including obscure ones like Chrome OS).
Ultimately, it doesn’t matter which of these options you pick — they’re all great. Just go with the one that you feel most comfortable with, and tell us in the comments below which one that was!
www.addictivetips.com
Методы анонимности в сети. Часть 4. Tor&VPN. Whonix / Хабрахабр
Всем привет!Вот мы и дошли до более интересных вещей. В этой статье мы рассмотрим варианты комбинирования Tor с VPN/SSH/Proxy. Для краткости далее я буду писать везде VPN, ведь вы все — молодцы и уже знаете плюсы и минусы VPN, SSH, Proxy, которые мы изучили ранее здесь и здесь. Мы рассмотрим два варианта подключений:
- сначала VPN, потом Tor;
- сначала Tor, а потом VPN.
Tor через VPN. Сначала VPN, потом Tor
VPN-сервер при такой схеме является постоянным входным узлом, после него шифрованный траффик отправляется уже в сеть Tor. На практике схема реализуется просто: сначала производится подключение к VPN-серверу, далее запускается Tor-браузер, который автоматически настроит нужную маршрутизацию через VPN-тоннель. Использование такой схемы позволяет скрыть сам факт использования Tor от нашего Интернет-провайдера. Также мы будем закрыты от входного узла Тора, который будет видеть адрес VPN-сервера. А в случае теоретической компрометации Tor, нас защитит рубеж VPN, который, разумеется, не хранит никаких логов. Использование вместо VPN прокси-сервера, лишено смысла: без шифрования, обеспечиваемого VPN, мы не получим каких-либо значимых плюсов в такой схеме.Стоит отметить, что специально для обхода запрета Tor интернет-провайдерами придумали так называемые bridges (мосты). Мосты – это такие узлы сети Tor, которые не занесены в центральный каталог Tor, то есть не видны, например, здесь или здесь, а, следовательно, труднее обнаруживаются. Как настроить мосты, подробно написано здесь. Несколько мостов может дать нам сам сайт Tor по адресу. Можно также получить адреса мостов по почте, отправив на адрес [email protected] или [email protected] письмо с текстом: «get bridges». Обязательно отправлять это письмо с почты от gmail.com или yahoo.com В ответ мы получим письмо с их адресами: «Here are your bridge relays: bridge 60.16.182.53:9001 bridge 87.237.118.139:444 bridge 60.63.97.221:443» Эти адреса нужно будет указать в настройках Vidalia – прокси-сервера Tor. Иногда происходит так, что и мосты блокируются. Для обхода этого в Tor введены так называемые «obfuscated bridges». Не вдаваясь в подробности, их труднее обнаружить. Чтобы к ним подключиться, надо, например, скачать, Pluggable Transports Tor Browser Bundle.
Плюсы схемы:
- мы скроем от Интернет-провайдера сам факт использования Tor (или подключимся к Tor, если его блокирует провайдер). Однако, для этого существуют специальные мосты;
- скроем от входного узла Tor свой ip-адрес, заменив его адресом VPN-сервера, однако это не самое эффективное повышение анонимности;
- в случае теоретической компрометации Tor, останемся за VPN-сервером.
- мы должны доверять VPN-серверу при отсутствии каких-либо значимых плюсов такого подхода.
VPN через Tor. Сначала Tor, потом VPN
В таком случае VPN-сервер является постоянным выходным узлом в сеть Интернет. Подобная схема подключения может использоваться для обхода блокировки узлов Tor внешними ресурсами, плюс она должна защитить наш траффик от прослушивания на выходном узле Tor. Существует немало технических сложностей в установлении такого подключения, например, вы же помните, что цепочка Tor обновляется раз в 10 минут или то, что Tor не пропускает UDP? Самый жизнеспособный вариант практической реализации это использование двух виртуальных машин (об этом чуть ниже). Важно также отметить, что любой выходной узел легко выделит клиента в общем потоке, так как большинство пользователей идут на разные ресурсы, а при использовании подобной схемы клиент идёт всегда на один и тот же VPN-сервер. Естественно, что использование обычных прокси-серверов после Tor не имеет особого смысла, так как траффик до прокси не шифруется.Плюсы схемы:
- защита от прослушивания траффика на выходном узле Tor, однако сами разработчики Tor рекомендуют использовать шифрование на прикладном уровне, например, https;
- защита от блокирования адресов Tor внешними ресурсами.
- сложная реализация схемы;
- мы должны доверять выходному VPN-серверу.
Концепция Whonix
Существует множество дистрибутивов ОС, основной целью которых является обеспечение анонимности и защиты клиента в Интернете, например, Tails и Liberte и другие. Однако наиболее технологичным, постоянно развивающимся и эффективным решением, реализующим самые передовые техники по обеспечению безопасности и анонимности, является дистрибутив ОС Whonix. Дистрибутив состоит из двух виртуальных машин Debian на VirtualBox, одна из которых является шлюзом, отправляющим весь траффик в сеть Tor, а другая – изолированной рабочей станцией, подключающейся только к шлюзу. Whonix реализует в себе механизм так называемого изолирующего прокси-сервера. Существует также вариант физического разделения шлюза и рабочей станции.Так как рабочая станция не знает свой внешний ip-адрес в Интернете, это позволяет нейтрализовать множество уязвимостей, например, если вредоносное ПО получит root-доступ к рабочей станции, у него не будет возможности узнать реальный ip-адрес. Вот схема работы Whonix, взятая с его официального сайта.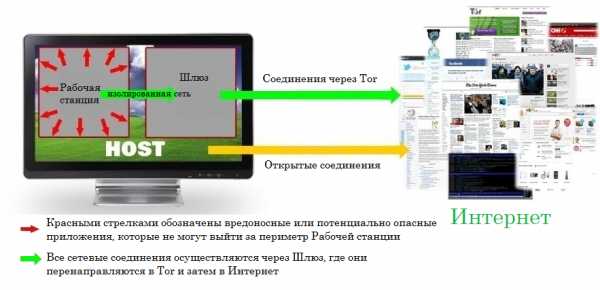 ОС Whonix, как утверждают разработчики, успешно прошла все возможные тесты на утечки. Даже такие приложения как Skype, BitTorrent, Flash, Java, известные своими особенностями выходить в открытый Интернет в обход Tor, также были успешно протестированы на предмет отсутствия утечек деанонимизирующих данных.
ОС Whonix реализует много полезных механизмов анонимности, я укажу наиболее важные:
ОС Whonix, как утверждают разработчики, успешно прошла все возможные тесты на утечки. Даже такие приложения как Skype, BitTorrent, Flash, Java, известные своими особенностями выходить в открытый Интернет в обход Tor, также были успешно протестированы на предмет отсутствия утечек деанонимизирующих данных.
ОС Whonix реализует много полезных механизмов анонимности, я укажу наиболее важные:
- весь траффик любых приложений идёт через сеть Tor;
- для защиты от профилирования траффика ОС Whonix реализует концепцию изоляции потоков. Предустановленные в Whonix приложения настроены на использование отдельного Socks-порта, а так как каждый Socks-порт использует отдельную цепочку узлов в сети Tor, то профилирование невозможно;
- обеспечивается безопасный хостинг сервисов «Tor Hidden services». Даже, если злоумышленник взломает web-сервер, то он не сможет украсть закрытый ключ «Hidden»-сервиса, так как ключ хранится на Whonix-шлюзе;
- Whonix защищен от DNS-утечек, так как в своей архитектуре использует принцип изолированного прокси. Все DNS-запросы перенаправляются на DnsPort Tor’а;
- Whonix поддерживает «obfuscated bridges», рассмотренные ранее;
- применяется технология «Protocol-Leak-Protection and Fingerprinting-Protection». Это снижает риск идентификации клиента через создание цифрового отпечатка браузера или системы путем использования наиболее часто применяемых значений, например, имя пользователя – «user», временная зона – UTC и т.д.;
- есть возможность туннелировать другие анонимные сети: Freenet, I2P, JAP, Retroshare через Tor, или работать с каждой такой сетью напрямую. Более подробные данные об особенностях таких подключений находятся по ссылке;
- важно отметить, что в Whonix протестированы, документированы и, главное, работают (!) все схемы комбинирования VPN/SSH/Proxy с Tor. Более подробную информацию об этом можно получить по ссылке;
- ОС Whonix – это полностью открытый проект, использующий свободное ПО.
- более сложная настройка, чем Tails или Liberte;
- требуются две виртуальные машины или отдельное физическое оборудование;
- требует повышенного внимания к обслуживанию. Надо следить за тремя ОС вместо одной, хранить пароли, и обновлять ОС;
- в Whonix кнопка «New Identity» в Tor не работает. Дело в том, что Tor-браузер и сам Tor изолированы по разным машинам, следовательно, кнопка «New Identity» не имеет доступа к управлению Tor. Чтобы использовать новую цепочку узлов, нужно закрыть браузер, изменить цепочку с помощью Arm, панели управления Тор, аналога Vidalia в Tor Browser, и запустить браузер снова.
Безопасность работы Whonix можно описать цитатой из его wiki: «And no, Whonix does not claim to protect from very powerful adversaries, to be a perfectly secure system, to provide strong anonymity, or to provide protection from three-letter agencies or government surveillance and such». Если вас ищут ведомства «их трёх букв», вас найдут :)
Вопрос дружбы Tor и VPN — неоднозначный. Споры на форумах по этой теме не утихают. Я приведу некоторые наиболее интересные из них:
- раздел о Tor и VPN с официальной страницы проекта Tor;
- раздел форума дистрибутива Tails по проблеме VPN/Tor с мнениями разработчиков Tails. Сам форум сейчас уже закрыт, но Гугл сохранил кеш обсуждения;
- раздел форума дистрибутива Liberte по проблеме VPN/Tor с мнениями разработчиков Liberte. Спасибо за внимание!
habrahabr.ru
COMBINING TOR WITH A VPN
Welcome back readers!
Today I want to talk about a greatly debated topic.
Should I use a VPN with TOR?Should I use TOR to connect to a VPN, or use a VPN to connect to TOR?
>>>Be sure to use a VPN with Tor. Click here for the best VPN’s<<<
Let me say first of all, that when you are browsing the internet without TOR, you should probably be using a VPN regardless of whether or not you are using TOR. And make sure that the VPN uses some form of encryption as well. For those of you who are very beginner, think about when you connect to a public wifi network at a coffee shop, or an airport and you get all these warnings that your requests sent over this network are vulernable.
All networks, but especially public wifi networks are vulnerable to traffic analysis. Put this together with the fact that some internet service providers monitor your activity to some level, and you can see why it might be a good idea to always use an encrypted method of using the internet. At the very least to protect your personal information when you are entering credit cards, usernames and passwords, as well as other personal data online. Again, especially if you are using a public wifi network.
Choosing a VPN that uses at least 128 bit encryption like TOR is good practice, and will stop the majority of eavesdroppers. But if you can get 256 bit encryption, you are even safer. Before we get into whether or not we should be using a VPN together with TOR, I want to give you a few warnings regarding how you should be using a VPN.
If you are going to be using a VPN for any type of freedom fighting, make damn sure that your VPN does not keep logs. This is actually a lot harder than you might think. Many VPN providers will claim to not keep logs of your activity in order to gain you as a customer, because they have to compete with the other providers out there. Customers are going to trend towards providers who offer no identifying data retention. Unfortunately, this claim of theirs is not always the real case and I will give you an example.
There is a well known VPN provider named HideMyAss that previously claimed not to keep logs of its users. Unfortunately, when met with a court order from their government in the UK, they handed over evidence of a suspected hacker from an internet group LulzSec which helped lead to his arrest. The story can be found below.
http://www.theregister.co.uk/2011/09/26/hidemyass_lulzsec_controversy/
One of the take home quotes from this article is the following.
We are not intimidated by the US government as some are claiming, we are simply complying with our countries legal system to avoid being potentially shut down and prosecuted ourselves.
A very smart man that goes by the online handle The Grugq, said when doing your freedom fighting online that nobody is going to go to jail for you, and he is 100% correct. When it comes down to it, no VPN provider is going to risk jail to protect a $20 a month subscriber. No matter how tough they sound, no matter how much they claim to care about protecting their customers, when faced with a choice to give you up or go to jail, they will always choose freedom.
Another thing to consider however, is using a VPN does hide your internet activity from your internet service provider. It can also hide the fact that you are using TOR, which may flag some suspicion when the feds start asking ISPs to provide data about their users. This may or may not be relevant, since many people use TOR and you can argue there are many legitimate reasons to use TOR and nothing suspicious about TOR. But it is just another factor to arouse suspicion that may or may not come into play and should be considered.
If you choose to use TOR over a VPN, the benefits are that you would be again, hiding from your ISP the fact that you are using TOR. Also, your VPN would only be able to see that you are connecting to TOR nodes and that you are sending encrypted data. The VPN would not be able to see what data you are sending over TOR unless they decrypted it, because remember, all information relayed over TOR is encrypted.
The downsides of course, as mentioned are that VPN providers may or may not log everything that you do in the form of meta data or even content if they have the storage capacity, and keep those logs on hand for a long time. In this case, it is no better than connecting to TOR through an ISP. Another thing to mention to those who will use VPNs when not using TOR, but also use VPNs when using TOR is remember when you are, and are not connected to your VPN. Sometimes VPNs can unexpectedly drop connections and you may not even be aware of it. If the reason you are using a VPN is to hide TOR activity from your ISP, then if your VPN drops, your ISP will start seeing your TOR traffic instead.
Or, maybe you forget that you are connected to your VPN and end up punching in your address on Google Maps to find directions somewhere. Well guess what Google does with all data entered into their system? They keep it. And they likely keep it indefinitely. So if one day the NSA identifies you on the TOR network by occupying a large number of nodes and using traffic analysis to identify you based on statistical analysis, it will link them to your VPN IP address.
At this point, they will likely ask the VPN to turn over data on their users, but if the VPN refuses to comply because they are not subject to US law, or the laws of other countries, they may check some of the big surveillance websites out there to see if you slipped up and used that IP address for anything else online. They will check logs from Google, Yahoo, Facebook, Twitter, Netflix and other big data collection companies to see who has been using that IP address to connect to their servers.
If you accidentally punched in your address on Google when connected to that VPN, you are now a suspect. So always keep things like this in mind. Just because you are covered behind a VPN does not mean you are not traceable by human error. The benefits of TOR, are that you get a new identity every time you connect. This may or may not be the case with your VPN, so please check and make sure.
Next post we will talk about the advantages and disadvantages of using TOR to connect to a VPN.
www.deepdotweb.com
|
|
..:::Счетчики:::.. |
|
|
|
|
|
|
|
|